Real-Time Security-Aware Routing with Network Traffic Visualization
This research project presents a comprehensive framework integrating dynamic security-aware routing (SAR-Dijkstra) and an interactive network traffic visualization dashboard. The system aims to enhance network security through proactive threat identification and optimized data routing based on real-time security assessments.
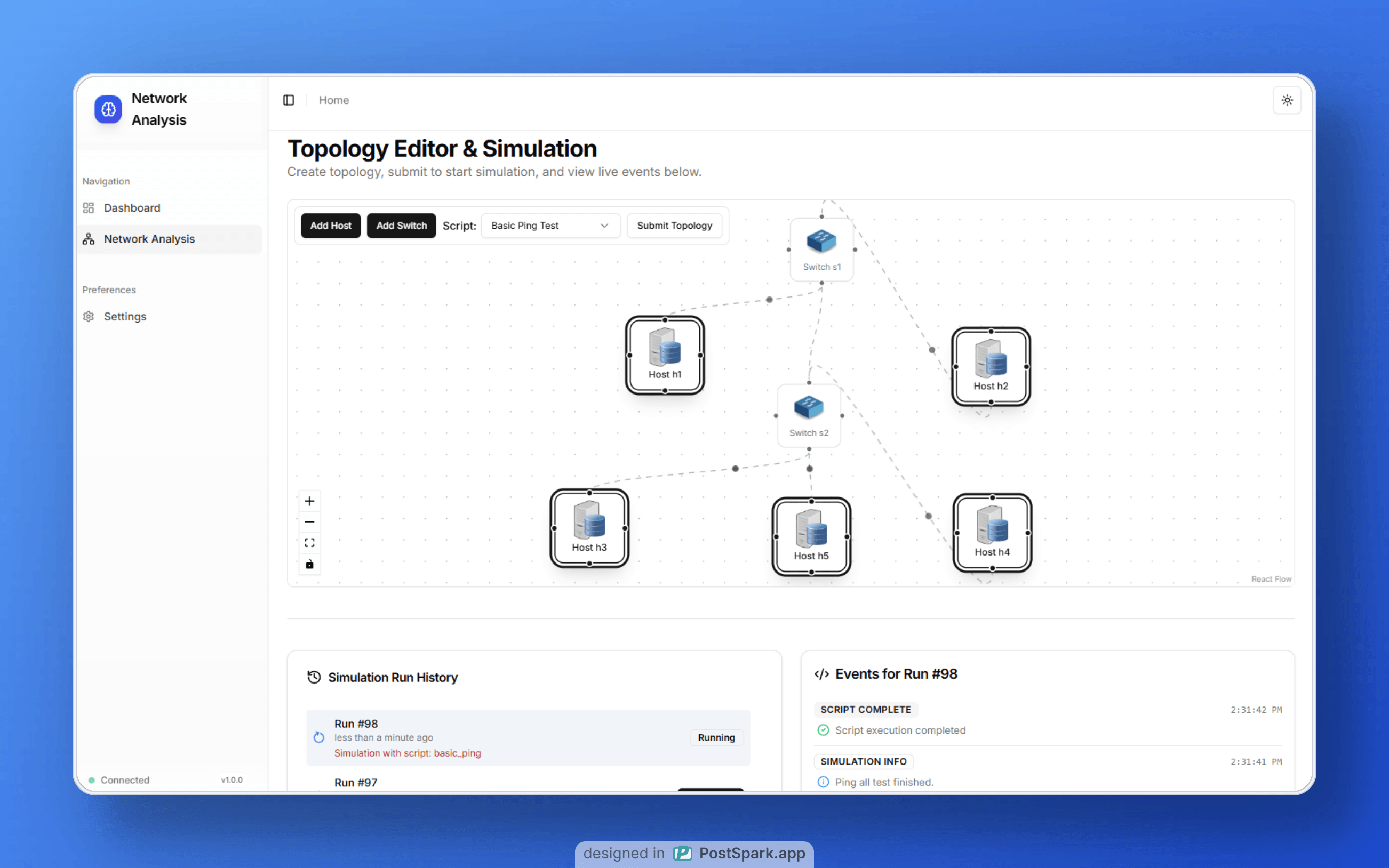
Framework Operational Flow
An overview of the sequential processing stages within the proposed network security framework, from data acquisition to responsive action and visualization.
Network Traffic Ingestion
Real-time capture of network packets from designated interfaces or virtual switches (e.g., Open vSwitch) for analysis.
Intrusion Detection (ML Analysis)
Machine learning models (e.g., Decision Tree, Random Forest) classify network flows to identify anomalies and potential threats based on extracted features.
Security Metric Calculation
Aggregate security metrics are computed based on IDS alerts, traffic characteristics, and node-specific parameters to quantify network risk levels.
SAR-Dijkstra Path Computation
The Security-Aware Routing algorithm (SAR-Dijkstra) calculates optimal forwarding paths considering the latest security metrics and network topology.
Flow Rule Deployment (SDN)
Calculated routes are translated into flow rules and deployed to network devices (e.g., switches) via an SDN controller interface.
Visualization & Monitoring
The system's state, including traffic patterns, detected threats, and active routes, is presented on an interactive dashboard for monitoring and analysis.

Core Components of the Research Framework
This section details the primary modules developed as part of this research, outlining their functionalities and contributions to the overall network security framework.

Machine Learning-Based Intrusion Detection System (IDS)
The proposed IDS employs machine learning models to identify and classify various network threats in real-time, including DDoS, Man-in-the-Middle, and ransomware attacks. The system is designed for continuous learning and adaptation to novel threat vectors, aiming for high detection accuracy and minimal false positives to maintain network integrity.

Dynamic Security-Aware Routing (SAR-Dijkstra)
The SAR-Dijkstra protocol is implemented to dynamically select optimal data transmission paths. It evaluates routes based on a combination of real-time security metrics, network latency, available bandwidth, and node trustworthiness. This approach aims to ensure data integrity, enhance resilience against path-based attacks, and maintain Quality of Service under diverse network conditions.

Interactive Network Traffic Visualization Module
A key component of this research is an interactive visualization dashboard designed to provide comprehensive insights into network operations. It allows for real-time monitoring of traffic flows, graphical analysis of detected threats (e.g., on topological maps), and clear representation of routing decisions. This module facilitates enhanced situational awareness, aids in rapid incident response, and supports network policy refinement and forensic investigations.
Overview of Implemented Features
This framework integrates several key components to address challenges in network security, focusing on machine learning for detection, adaptive routing, and comprehensive visualization.
Machine Learning-Based Intrusion Detection
Utilizes machine learning models for real-time detection of diverse network threats, including DDoS, MitM, and ransomware attacks.
Security-Aware Routing (SAR-Dijkstra)
Dynamically optimizes network paths based on real-time security metrics, aiming to ensure data integrity and Quality of Service.
Interactive Visualization Dashboard
Provides insights into network traffic, detected threats, and routing decisions through a comprehensive, user-friendly interface for analysis.
Comprehensive Threat Pattern Analysis
Analysis of network traffic patterns to identify and classify malicious flows, leveraging detailed feature engineering techniques.
Automated Mitigation via SDN Integration
Integration with Software-Defined Networking (SDN) controllers for the automated deployment of flow rules to mitigate identified threats.
Scalable and Modular Design Considerations
The framework is designed with considerations for scalability and modularity, potentially employing a microservices-based approach for efficient resource utilization.